Strengthening Security in Distributed Grid Computing Environments
As grid computing continues to evolve, providing organizations with vast computational power and resource-sharing capabilities, security has become an increasingly critical concern. Unlike traditional computing models, grid computing operates in a distributed manner, connecting multiple nodes—often across different geographical locations—to process large-scale computations. While this model enhances efficiency, scalability, and cost-effectiveness, it also introduces complex security risks that can expose sensitive data, compromise system integrity, and allow unauthorized access.
Grid computing environments lack a centralized control system, making them more vulnerable to data breaches, cyberattacks, and misuse of computing resources. Attackers can exploit weak authentication measures, intercept sensitive data during transmission, or launch distributed denial-of-service (DDoS) attacks against grid infrastructures. Without proper security strategies, grid computing networks can become entry points for cyber threats that compromise not only data but also computational tasks and research collaborations.
This article explores the key security challenges in grid computing, including data privacy risks, access control issues, and network vulnerabilities, followed by mitigation strategies and best practices to ensure a secure grid computing environment.
Understanding Security Challenges in Grid Computing
The distributed nature of grid computing makes it inherently more vulnerable than centralized computing models. Unlike traditional IT systems, where security protocols can be enforced within a single organization, grid computing spans multiple institutions, networks, and administrative domains. Each of these domains may have different security policies, creating inconsistencies that can be exploited by cybercriminals.
One of the biggest challenges is ensuring that only authorized users have access to grid resources while preventing unauthorized intrusions. With multiple nodes processing data simultaneously, there is always a risk that sensitive information could be intercepted, altered, or stolen. Furthermore, as grid computing enables resource sharing, malicious actors can attempt to misuse computing resources for illicit activities, such as cryptojacking or executing cyberattacks.
Another pressing issue is the management of user credentials and authentication across distributed nodes. Traditional password-based authentication is often insufficient in grid computing environments because attackers can steal credentials and gain access to multiple systems at once. Therefore, security must be multilayered, involving strong authentication mechanisms, encrypted communications, and real-time monitoring of grid activities.
Key Security Challenges
Data Privacy and Integrity
One of the most critical security concerns in grid computing is data privacy. Since grid environments handle large volumes of sensitive data, including scientific research, financial transactions, and personal records, ensuring data confidentiality is paramount. Without proper safeguards, data can be:
- Intercepted during transmission, leading to leaks of sensitive information.
- Tampered with or altered, causing research inaccuracies or system failures.
- Accessed by unauthorized parties, violating compliance regulations such as GDPR and HIPAA.
To mitigate these risks, strong encryption techniques should be employed for both data in transit and data at rest. Secure communication protocols, such as TLS (Transport Layer Security) and end-to-end encryption, help prevent unauthorized access and data leaks.
Authentication and Authorization
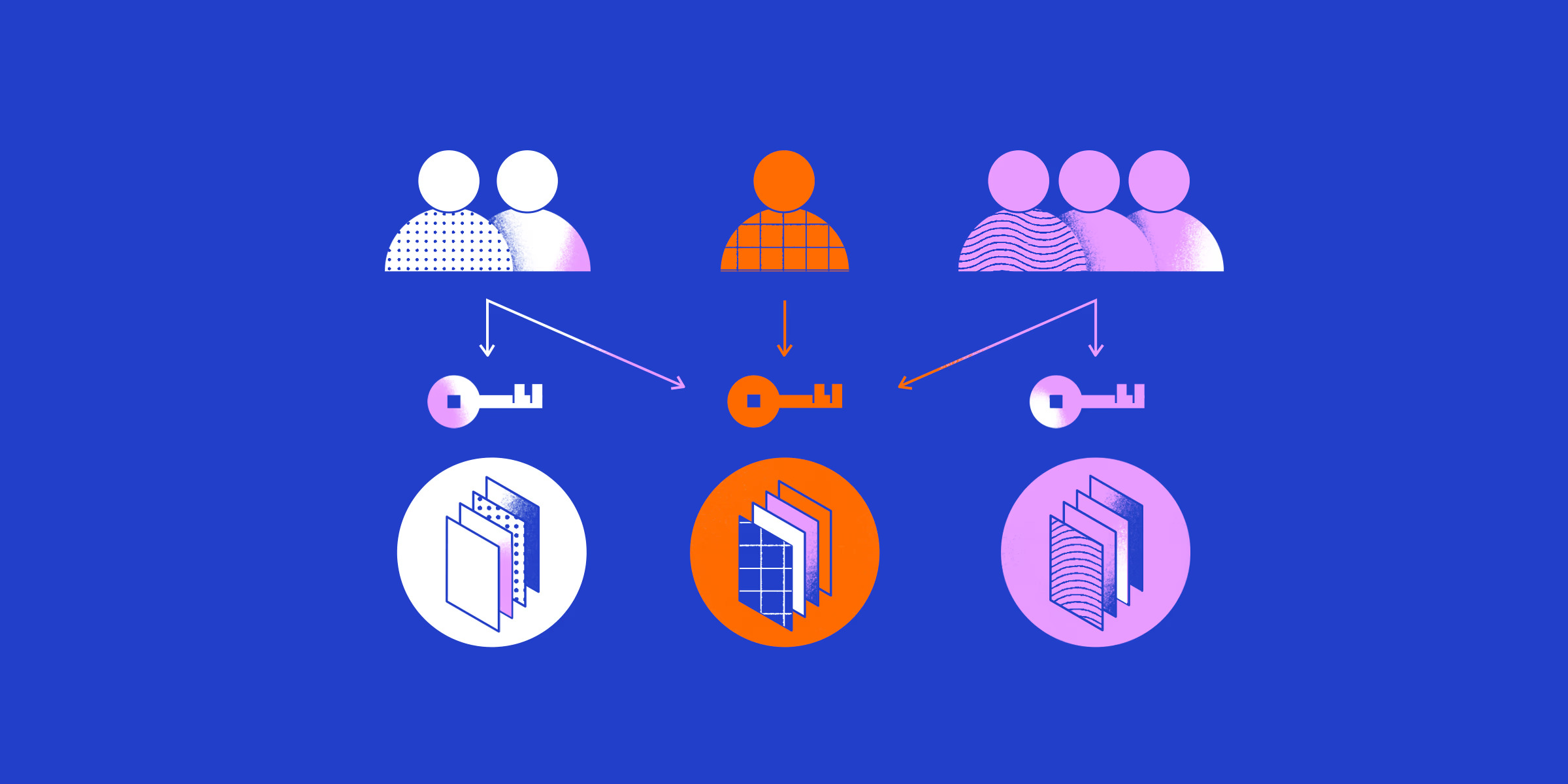
Grid computing requires robust user authentication and access control mechanisms to prevent unauthorized users from accessing computational resources. However, securing authentication in a distributed environment presents challenges, including:
- Managing credentials across multiple administrative domains, making it difficult to enforce uniform security policies.
- Ensuring that only authorized users can submit computational jobs, preventing system abuse.
- Verifying user identities without introducing excessive complexity that slows down grid operations.
One effective approach to reducing credential theft and phishing risks is using temporary email for cybersecurity. Temporary email services help protect user credentials by minimizing exposure to phishing attacks and preventing unauthorized access through compromised email accounts.
Role-Based Access Control (RBAC) is a widely adopted method to restrict access based on predefined user roles. This ensures that users only have the permissions necessary for their tasks, reducing the risk of privilege escalation. Multi-factor authentication (MFA) also enhances security by requiring multiple forms of identity verification before granting access.
Network Security Risks
Since grid computing relies heavily on inter-node communication, securing network connections is crucial to prevent unauthorized access, interception of data, and denial-of-service (DDoS) attacks. Potential threats include:
- Man-in-the-middle (MITM) attacks, where cybercriminals intercept and manipulate data transfers.
- DDoS attacks, which can overwhelm grid computing resources, leading to service disruptions.
- Exploitation of insecure communication channels, allowing attackers to inject malicious code into the system.
To address these risks, firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) should be deployed to protect network communications and prevent cyberattacks.
Mitigation Strategies for Security Risks
Addressing security challenges in grid computing requires a multi-layered approach that integrates encryption, authentication, monitoring, and intrusion prevention mechanisms.
Implementing Strong Encryption Protocols
All data transfers within the grid network should be encrypted to prevent interception and tampering. Using AES-256 encryption for stored data and TLS/SSL for transmission ensures that sensitive information remains protected even if intercepted by attackers.
Using Multi-Factor Authentication (MFA) for Access Control
To enhance security, organizations should implement multi-factor authentication (MFA), requiring users to verify their identity using a combination of passwords, biometric authentication, and one-time verification codes. This significantly reduces the risk of credential theft and unauthorized access.
Regular Monitoring and Security Audits
Continuous monitoring of grid computing environments helps detect and mitigate potential threats before they escalate. Implementing Security Information and Event Management (SIEM) tools enables real-time tracking of suspicious activities and anomaly detection.
Regular security audits and penetration testing can identify vulnerabilities and ensure compliance with security best practices.
Deployment of Firewalls and Intrusion Detection Systems (IDS)
Firewalls should be configured to block unauthorized access, while Intrusion Detection Systems (IDS) can monitor for suspicious activity and potential attacks on grid nodes. Additionally, VPNs and secure tunneling should be used to encrypt data transmissions between grid nodes.
Best Practices for Securing Grid Computing Environments
Implementing Secure Grid Middleware Configurations
Middleware acts as the bridge between different nodes in a grid environment. Ensuring that middleware settings are securely configured, updated regularly, and protected against vulnerabilities is crucial for preventing cyberattacks.
Training Users and Administrators in Security Awareness
Many security breaches occur due to human error. Educating researchers, developers, and administrators about security best practices, phishing threats, and safe computing habits can significantly reduce risks.
Regular Software Updates and Patches
Cybercriminals often exploit unpatched software vulnerabilities to gain unauthorized access. Keeping all grid computing software, operating systems, and security tools up to date helps protect against known threats.
Emerging Security Solutions for Grid Computing
As security threats evolve, new technologies are emerging to enhance protection in grid computing environments.
AI-Driven Threat Detection and Response
Artificial intelligence (AI) and machine learning are being used to detect anomalies, identify cyber threats in real-time, and automate security responses in grid computing systems.
Blockchain-Based Identity Management
Blockchain technology offers decentralized identity management, making it more difficult for attackers to forge credentials or gain unauthorized access.
Secure Cloud-Grid Hybrid Approaches
Hybrid models that combine cloud computing with grid systems allow organizations to leverage cloud security protocols while maintaining the distributed nature of grid computing.
Ensuring a Secure Future for Grid Computing
Security remains one of the biggest challenges in the adoption and expansion of grid computing systems. Without proper safeguards, grid environments remain vulnerable to data breaches, unauthorized access, and cyberattacks. However, by implementing strong encryption, access control measures, continuous monitoring, and emerging security technologies, organizations can mitigate risks and protect their grid infrastructure.
As grid computing continues to evolve, the need for advanced security solutions and proactive defense strategies will only grow. Researchers, IT professionals, and organizations must stay ahead of cyber threats and ensure that grid computing remains a secure and reliable tool for scientific research and enterprise applications.